
CIPS CONNECTIONS
Interviews by Stephen Ibaraki, I.S.P., DF/NPA, CNP, MVP
Bruce Schneier: World's Foremost Security Technologist; Celebrated Recipient of the Secure Computing Lifetime Achievement Award; InfoWorld’s CTO of the Year...
This week, Stephen Ibaraki, I.S.P., has an exclusive interview with Bruce Schneier, unquestionably the world’s foremost security technologist, and Founder and Chief Technical Officer for Counterpane Internet Security, Inc.
Amongst his many accomplishments, in 2005, InfoWorld named Bruce a CTO of the Year, and in 2003, an independent panel of judges awarded Bruce the Secure Computing Lifetime Achievement Award. Previous winners have included Rivest, Shamir, and Adleman, the three founders of RSA.
Due to his world-renowned expertise, Bruce has testified before the Homeland Security Subcommittee and has provided his elite services to groups as diverse as the American Civil Liberties Union and the Electronic Frontier Foundation. Bruce is at the forefront of security technologies and processes, including inventing outsourced security monitoring and the Blowfish and Twofish encryption algorithms.
Bruce’s free monthly e-mail newsletter, Crypto-Gram is the most widely read security newsletter, with more than 120,000 readers.
Bruce’s first book, Applied Cryptography, the seminal work in its field, has sold more than 200,000 copies, and has been translated into five languages. Secrets & Lies: Digital Security in a Networked World is his book about computer and network security, a best seller with more than 80,000 copies sold. His most recent book, published in September 2003, is Beyond Fear: Thinking Sensibly About Security in an Uncertain World. It tackles both the big and small problems of security: home security, homeland security, counterfeiting, terrorism, etc., and has garnered wide attention and a faithful following.
The latest blog on the interview can be found on February 7th, 2006 in the Canadian IT Managers forum where you can provide your comments in an interactive dialogue: http://blogs.technet.com/cdnitmanagers/
Discussion:
Bruce, you are widely acknowledged as the world’s top authority in Internet security, so we are indeed privileged you have taken time out of your schedule to do this interview. Thank you for sharing your accumulated wisdom with our audience.
Q: From our last discussion in 2003, can you update us on your work with encryption algorithms?
A: Lately I’ve been working on stream ciphers. It seems that on a purely abstract level, stream ciphers are more efficient than block ciphers. That is, it takes fewer clock cycles to encrypt a byte of data with a stream cipher than it does with a block cipher. I have some guesses about why this is true, but nothing concrete yet.
Two specific designs came out of this work: Helix and Phelix. Both are stream ciphers and both have the interesting property of computing a MAC (message authentication code) at the same time as they encrypt or decrypt data. This makes them super-efficient when you need to both encrypt and MAC data, which turns out to be quite a lot of the time.
Q: Tell us more about Counterpane joining the Sourcefire Certified Snort Integrator program.
A: Counterpane has always been a strong supporter of open source programs, as well as groups that create free utilities that allow for a wider adoption of a layered security approach. One problem is that sometimes organizations that began as developing open source programs create and launch commercial companies. When this happens, they often abandon the open source programs, leaving the user communities with solutions that cannot continue to grow and expand. Of course, they hope that the communities buy the new commercial version.
Sourcefire did not do that. They didn’t abandon the open source community. So they created the "Sourcefire Snort Integration Program" to engage the larger security community and organizations that have utilized Snort over the years and built a high level of support and expertise. Counterpane is proud to continue to contribute to the Snort efforts and participate with Sourcefire at this professional level.
Q: How do you see digital identity theft evolving into the future and the means for thwarting it?
A: Identity theft is a terrible name; your identity is the one thing about you that cannot be stolen. I think of this type of crime as fraud: fraud due to impersonation. It is a fast-growing area of crime, and likely to continue to grow in the future.
Impersonation fraud is so pervasive for two reasons. One, identity information is easy to obtain. And two, identity information is incredibly valuable once obtained. Most of the “solutions” propose focus on the first problem and are not very successful. I think we need to focus on the second.
And I think we need to fix the underlying economic failure. As long as impersonation fraud is largely an externality to banks and data brokers, they won’t spend the money to secure their systems. I support laws that make financial institutions liable for the effects of this type of fraud.
I have written extensively about this.
Q: Can you apply the same question to data theft?
A: Data theft is a more general problem. It includes thefts of large amounts of personal data from data brokers like ChoicePoint, but it also encompasses industrial espionage and similar attacks. I see this type of crime continuing for the foreseeable future, as we don’t have any good means to secure computers and networks. Certainly those who invest in security products and services can be largely secure from these types of attacks, but many organizations don’t bother.
Q: You created a worldwide early-warning system for responding quickly to attacks on corporate infrastructure. Can you comment on how this works and how your processes and technologies will evolve into the future?
A: Our early detection capability for zero-day attacks on corporate networks is a function of our ability to correlate data across 550 networks worldwide; more specifically, analyze activity patterns down to an individual device (e.g., a firewall, router, or host). While the activity on any given network can change based on legitimate or malicious activity, it is uncommon to see similar changes in behavior across many different networks.
For example, during the Zotob outbreak, we detected an increase in NetBIOS activity across many networks simultaneously. What was interesting about Zotob was that the increase in network activity was very subtle - unlike previous worms - because the method Zotob used to scan for vulnerable hosts looks like legitimate Windows traffic. But by correlating the change in activity from many different networks, we can detect this type of thing. We can actually see the early formation of a worldwide zero-day attack.
Our plans are to do even better. We are currently working on improving our behavior detection within a variety of business applications at the user level. We are working on expanding our application level support, and correlating this information with everything else we see on the network. This is a type of monitoring that IDSs and IPSs cannot do, because they are only looking at the identity of network traffic and not its content. For example, today we can profile the login activity for a given user, such as “administrators” at each Windows host. We can profile based on certain criteria, such as time of day and frequency. While it is possible that any given host can deviate from its historical profile, (e.g., planned maintenance), if we detect a cluster of activity that is all outside the behavior profile, (especially if we see this worldwide across different networks), we would have a strong indication that an attack is in progress. Today we can apply this to some applications (databases, SAP, etc); we will continue to expand this to include other business applications as well.
Q: In 2003, Counterpane was rolling out several new services: a vulnerability scanning service, which provides additional information about the customer’s network allowing you to monitor them better; a device management service, which also works in concert with monitoring; and Active Response, where Counterpane takes defensive actions on behalf of the customer in the event of a security incident.
What are your future plans for Counterpane in 2006 and 2007?
A. For 2006, Counterpane is heavily focused on changing the rules on how MSSPs report data back to customers. Counterpane has always been the acknowledged visionary in the MSSP space - just ask Gartner - and we will continue to provide services that benefit our customers while challenging our competitors. In the past, MSSPs have been very tech-oriented in their reporting; lots of details about esoteric things, with a healthy measure of why-it's-important analysis. This works best if the customers at the other end - the people who actually hired us - are in a position to make use of this kind of detail. This is definitely a core benefit of our services when we interact with a technical audience.
Where we want to expand is into business information reporting. This means fewer individual events with less granular detail, but more dollars-and-cents information. We will continue to offer flexibility, so we're working on a lot of different mechanisms for tracking running incident costs. This is based on factors such as whether or not there's a positive indication that an attack was “successful” in some way, how quickly the customer reacted, and what Counterpane could do for that client, based on its services mix and deployment scope, to reduce the costs for that incident type in the future.
There are lots of detail updates to existing services planned for 2006 as well. Counterpane has launched numerous services into the marketplace in the past two years and our general plan is to deepen the pool of service expertise for the next 12 months – to stay ahead of our customers' expectations. You’ll see us making announcements about all-new services as 2006 draws to a close and we can expand the envelope of what a full-service MSSP should be.
Q: What do you see as the biggest crisis in security for 2006 and how should enterprises prepare?
A: Crime. The big thing on the Internet is crime. This has been true for about two years now and will continue to be true through 2006.
Defending against computer crime is not really any different than defending against hackers. You need good security products. You need 24x7 security monitoring. You need processes in place. There are differences in the types of attacks, but they are less important.
I’ve written about the characteristics of criminal attacks and general attack trends here.
Q: Can you share three case studies illustrating the vulnerabilities of corporations?
Case 1: Sony BMG Root Kit
On 17 November 2005 at 5:30 PM, the Counterpane SOC notified one of its customers, a large global mortgage insurer, that it saw evidence of the Sony BMG Rootkit active on one of its networks. The customer called back an hour later to confirm the activity. It had been testing its Trend Micro Anti-Virus / Anti-Spyware system to see if it would detect the Sony BMG Root kit. The anti-virus / anti-spyware system failed to detect the rootkit, but the customer was relieved to receive an alert notification from the Counterpane SOC.
The discovery of this Internet epidemic is credited to one man: Mark Russinovich. On 31 October 2005, Russinovich published to his Sysinternals web log his discovery of finding the Sony BMG rootkit residing hidden, within his PC.
Essentially, Sony installed its Digital Rights Management (DRM) software on Russinovich’s computer when he played one of its music CDs. The music CD installed the DRM software without Russinovich’s knowledge and hid it from his standard malware detectors, like anti-virus and spyware, using the same techniques that hackers typically use to install rootkits.
Russinovich’s subsequent research and web log publication over the next few weeks slowly gained traction in the mass media, but not with the traditional security companies. I wrote about it in a Wired column: “But much worse than not detecting it before Russinovich's discovery was the deafening silence that followed. When a new piece of malware is found, security companies fall over themselves to clean our computers and inoculate our networks. Not in this case.”
On 16 November 2005, Counterpane’s Threat Intelligence Group began assessing the risk associated with the Sony Rootkit and realized that none of the major Intrusion Detection vendors had developed or deployed standard signatures to detect the rootkit’s presence. ISS published TRONS rules, and Bleeding Edge Snort published proof of concept rules, but none were part of the standard IDS packages.
Counterpane’s Device Management group modified the Bleeding Edge SNORT signatures to work best with the Counterpane-deployed Snort IDS engines. They deployed those rules on 17 November 2005 about the same time that Counterpane’s Network Intelligence Group published its Risk Assessment.
When the global mortgage insurer customer received the Risk Assessment from Counterpane, it resolved to check if its anti-virus / anti-spyware system would catch the presence of the root kit. As stated before, its systems did not detect it, but because the customer also uses the Counterpane monitoring service, it was covered.
Counterpane’s ability to detect this type of security event demonstrates the professionalism and expertise inherent in the Counterpane system, and just one way in which we do our job.
Case 2: Unannounced Penetration Testing by Customer
On 13 April 2005, a customer complained to the SOC Director that Counterpane had missed an unannounced Penetration Test during the week of 5–11 Apr. After review of the audit trail, Counterpane showed the customer that the SOC did indeed warn it of suspicious activity on three separate occasions and even told it that the attacker might be trying to fly below the radar.
1. At 9:43 AM on 5 April, five minutes after initial contact, Counterpane contacted the customer regarding the following alert discovered by its NetRanger Intrusion Detection System (IDS): “Suspicious Mail Attachment: NetRanger 3110-0. ”
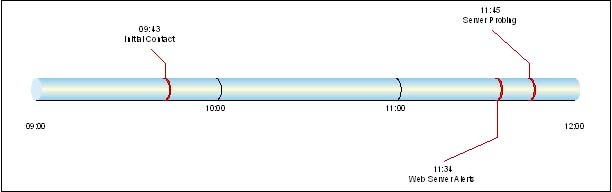
The “Suspicious Mail Attachment: NetRanger 3110-0” signature fires when the IDS discovers attachments with the following file extensions: ".vbs", ".vbe", ".wsf", ".wsh", ".hta". IDS vendors first associated this vulnerability with the Love Letter VBScript mail worm launched in May of 2000. Although the Socrates system captured only two alerts within this initial ticket, Counterpane still wanted the customer to check this event.
2. Two hours later, Counterpane sent another e-mail to the customer, advising it of more peculiar activity. Counterpane had observed a number of alerts generated from its IDS devices directed at its Web server. This kind of activity is typical of a directed scan against a single internal host. Counterpane captured 25 IDS alerts of this type within two hours.
3. Fifteen minutes later, Counterpane notified the customer again regarding multiple instances of direct probing against other servers on their internal network.
This activity came from the same external host IP address as the previous attacks and confirmed that the attacker had more in mind than just a random scan. The Counterpane analyst reported to the customer: “Low volume probing events have been originating from the above source every few/several minutes as if they are attempting to "fly below radar". That or they just may be slow typers. Please investigate the source.”
After review of the audit trail, the customer conceded that Counterpane did in fact alert it to the Unannounced Penetration Test in a timely manner and that it needed to review its internal procedures more closely to take advantage of the Counterpane service.
Case 3: MS-SQL Worm Attack
On 19 April 2005 at 3:25:07 PM EST, 11 minutes after the initial contact, the SOC contacted a customer regarding an “MS-SQL version overflow attempt” alert triggered by the customer’s Snort Intrusion Detection System (IDS). The IDS sent 30 alerts in the first five minutes.
“The MS-SQL version overflow attempt” alert fires when the Snort IDS engine sees a potential buffer overflow attempt.
Versions of Microsoft’s implementation of SQL server running the resolution service are subject to multiple buffer overflows that could result in a Denial of Service (DOS) or remote code execution. The SQL Slammer (Sapphire) worm exploited these vulnerabilities when attackers launched it in January of 2003.
Thirty seconds later, Counterpane contacted the customer again regarding the same MS-SQL Worm propagation activity, after another 32 alerts from the customer-owned IDS engine.
One minute after that, Counterpane contacted the customer once again regarding more MS-SQL Worm propagation activity; this time another 33 alerts were received from the IDS.
Just under an hour later, Counterpane finally communicated the problem to one of the customer’s security engineers over the phone, who said that he would look into the problem.
20 minutes later, Counterpane received a call from a second security engineer requesting more information. He did not know the pass phrase and therefore received no information from Counterpane.
Three minutes later, the original customer security engineer called back with the proper pass phrase to verify if Counterpane was still seeing worm activity. Counterpane confirmed. The customer said that he was still looking into it.
At 5:16:58 PM EST, the customer called Counterpane to verify that the worm had stopped. He had identified a home dial-up user going through the corporate VPN who was the source of the worm activity. He disconnected that user from the network and the worm stopped.
Q: What do you foresee as the major competing security technologies in the enterprise space in three years; what are their strengths and weaknesses? Who will be the big losers? How should businesses prepare for these changes?
A: Security is no longer about technology. It’s about people. It’s about economics. Companies should prepare for a time when they are responsible for security breaches, not just for their own data, but the data of others.
Q: You have spoken at many forums and events. Which ones would you recommend our audience to attend, and for what reasons?
A: There are a lot of mediocre security conferences out there. Right now, I think the best is the RSA Conference; but honestly, it’s the best of a mediocre lot. I’m speaking at the next one in San Jose, February 2006.
Q: You have never been one to avoid controversy so now choose any topics of your choosing and provide commentary.
A:
- Topic 1: Airport security and metal knives
- Topic 2: Voting security
- Topic 3: The security of police oversight
- Topic 4: Terrorists and “movie-plot threats”
- Topic 5: Why profiling doesn’t work
Final Comment: Bruce, it is always a real pleasure and delight in discussing the area of security with you. Your work continues to be followed by hundreds of thousands of senior security specialists due to your elite standing.